Setting Up A Virtual Machine Hacking Lab: Difference between revisions
Duffsigpatch (talk | contribs) No edit summary |
Duffsigpatch (talk | contribs) |
||
| (18 intermediate revisions by the same user not shown) | |||
| Line 16: | Line 16: | ||
==Setting Up A Network== | ==Setting Up A Network== | ||
In order to test out vulnerabilities in software, you must first configure your virtual machines in such a way that they can talk to each other. This involves setting up an internal network of virtual machines with '''DHCP''' (Dynamic Host Configuration Protocol). DHCP is what gives us an IP address when we connect to something like a router. | |||
There is an option to do it without DHCP and assign IP addresses manually, but that would be an extra step, and any time you use a new machine you'd have to configure it so that it has an IP address. | |||
Setting up a DHCP network is easy. It's one command in the command prompt: | |||
<code>VBoxManage dhcpserver add --netname intnet --ip 10.0.2.0 --netmask 255.255.255.0 --lowerip 10.0.2.2 --upperip 10.0.2.254 --enable</code> | |||
This adds DHCP to the virtual network known as intnet. The "10.0.2.0" and "255.255.255.0" specifies the subnet 10.0.2.0 as the network. Lowerip and upperip specify the range of addresses to assign. Finally, enable says to enable it. | |||
====Attaching Network To A VM==== | |||
[[File:Screenshot_2024-03-18_09-41-07.png]] | |||
[[File:Screenshot_2024-03-18_09-42-03.png]] | |||
[[File:Screenshot_2024-03-18_09-42-47.png]] | |||
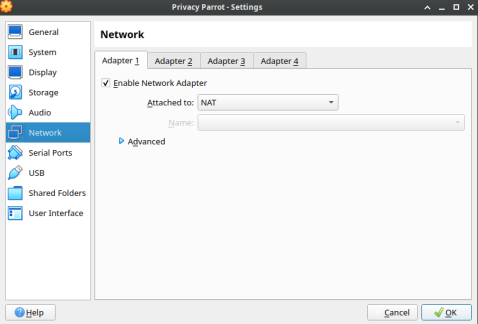
#Head to Network Settings for the VM. | |||
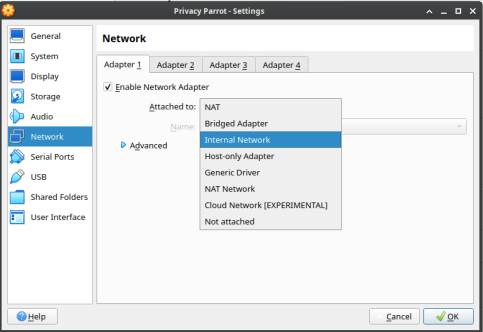
#Select Internal Network. | |||
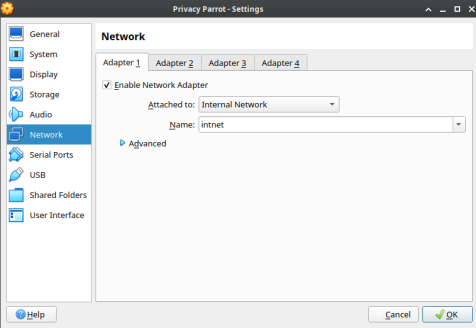
#Put in the name of the internal network. | |||
It is worth noting if this is the only network adapter you attach, you won't be able to reach the internet. You will need to attach a separate NAT adapter if you want to be able to reach the internet. | |||
==Alternatives== | |||
Hacking on a flat network is fun at first, but over time, you may begin to notice that it is very hard to completely secure a system if the attacker is already in a network. Luckily, Virtual Machines can also act as a Router/Firewall. It is, unfortunately, not user friendly. I spent hours myself trying to get it working. I got it working however. And, good news for you, that means that I can give you a massive shortcut by offering you [https://drive.google.com/file/d/1O8Cw1bNDwYhLwnl33y5lQ7KNq7ntjoy0/view?usp=sharing this] OVF file (the default password is 'changeme'). | |||
This is a preconfigured version of OpenWRT, a version of BSD designed to be used as routing software. It is set up with an internal interface that Virtualbox called 'firewall' that you can simply connect to from other VMs while the router is running. The other interface might need some tweaking, but set it up as a Bridged Adapter and set it to use your wireless connection. This will essentially make it so the router is the gateway all VM traffic passes through to get to the network you have your home router set up on. You can access the router from your home network too by typing in the IP address assigned to the bridge adapter into a browser. Same as you can do inside a VM if you type the gateway address. All you have to do is login with the password above. | |||
I installed some tools on the VM to help out. First, I installed Nano because VI sucks. Second I installed TCPDump to try and aid in debugging efforts. I also configured the router to use Google DNS, as it's probably one of the better options that will universally work. | |||
Also, in order for this scenario to work, connect your attacker to your local internet with a bridged adapter and not the firewall internal network. The way the simulation works is that your attacker is outside the network trying to get in, not already inside wreaking havoc. | |||
==Happy Hacking== | |||
Enjoy your machine lab. Now that you got it set up, you have a place to practice hacking skills. If you are feeling a little more adventurous, you can also quarantine a VM and load it full of malware to get an idea of what the malware is doing. Be careful though. | |||
'''Caution: It is worth noting that something like Metaspoitable should not be connected to the internet if it is not behind a firewall as it is vulnerable. Even with a firewall, don't do much web browsing on it because it could be vulnerable to web based attacks. Or better yet, turn off internet to the firewall in Virtualbox itself.''' | |||
Latest revision as of 14:52, 7 May 2024
Virtual Machines form the backbone of AWS and many other services in the industry, but that is not the point of this article. The point of this article is to help you set up a method for you to play around with hacking into things. You will need enough ram to run 2 machines at once if you're gonna do this. Without further ado, let's get started.
Installing Virtualbox and Getting Your Machines
Virtualbox is the software we'll be doing this with. It can be downloaded here. Run the program and install Virtualbox.
We'll need a pre-built virtual machine for both an attacker and a defender. You have options for both these things.
Some prominent hacking distributions of Linux that you can use for your hacking lab are:
For systems to attack, the best one is probably Metasploitable, because its preloaded with vulnerabilities, but you can always configure your own system to be vulnerable and try to break into it. A good resource if you do this would be STIGs, which are step by step guides of how to harden a system with default settings.
Setting Up A Network
In order to test out vulnerabilities in software, you must first configure your virtual machines in such a way that they can talk to each other. This involves setting up an internal network of virtual machines with DHCP (Dynamic Host Configuration Protocol). DHCP is what gives us an IP address when we connect to something like a router.
There is an option to do it without DHCP and assign IP addresses manually, but that would be an extra step, and any time you use a new machine you'd have to configure it so that it has an IP address.
Setting up a DHCP network is easy. It's one command in the command prompt:
VBoxManage dhcpserver add --netname intnet --ip 10.0.2.0 --netmask 255.255.255.0 --lowerip 10.0.2.2 --upperip 10.0.2.254 --enable
This adds DHCP to the virtual network known as intnet. The "10.0.2.0" and "255.255.255.0" specifies the subnet 10.0.2.0 as the network. Lowerip and upperip specify the range of addresses to assign. Finally, enable says to enable it.
Attaching Network To A VM
- Head to Network Settings for the VM.
- Select Internal Network.
- Put in the name of the internal network.
It is worth noting if this is the only network adapter you attach, you won't be able to reach the internet. You will need to attach a separate NAT adapter if you want to be able to reach the internet.
Alternatives
Hacking on a flat network is fun at first, but over time, you may begin to notice that it is very hard to completely secure a system if the attacker is already in a network. Luckily, Virtual Machines can also act as a Router/Firewall. It is, unfortunately, not user friendly. I spent hours myself trying to get it working. I got it working however. And, good news for you, that means that I can give you a massive shortcut by offering you this OVF file (the default password is 'changeme').
This is a preconfigured version of OpenWRT, a version of BSD designed to be used as routing software. It is set up with an internal interface that Virtualbox called 'firewall' that you can simply connect to from other VMs while the router is running. The other interface might need some tweaking, but set it up as a Bridged Adapter and set it to use your wireless connection. This will essentially make it so the router is the gateway all VM traffic passes through to get to the network you have your home router set up on. You can access the router from your home network too by typing in the IP address assigned to the bridge adapter into a browser. Same as you can do inside a VM if you type the gateway address. All you have to do is login with the password above.
I installed some tools on the VM to help out. First, I installed Nano because VI sucks. Second I installed TCPDump to try and aid in debugging efforts. I also configured the router to use Google DNS, as it's probably one of the better options that will universally work.
Also, in order for this scenario to work, connect your attacker to your local internet with a bridged adapter and not the firewall internal network. The way the simulation works is that your attacker is outside the network trying to get in, not already inside wreaking havoc.
Happy Hacking
Enjoy your machine lab. Now that you got it set up, you have a place to practice hacking skills. If you are feeling a little more adventurous, you can also quarantine a VM and load it full of malware to get an idea of what the malware is doing. Be careful though.
Caution: It is worth noting that something like Metaspoitable should not be connected to the internet if it is not behind a firewall as it is vulnerable. Even with a firewall, don't do much web browsing on it because it could be vulnerable to web based attacks. Or better yet, turn off internet to the firewall in Virtualbox itself.